We plug our phones in to charge at home, at work, at Starbucks, at the airport, and wherever we need to charge. Rarely do we consider the security ramifications of plugging a device into an unknown charger.
Summary
Take Charge leverages Android's USB keyboard support to emulate keystrokes and surreptitiously download and install a data mining application when a device is plugged into USB, without the user knowing. Once this application is installed, it can track the user's location, monitor notifications, and access contacts. The data from all compromised devices is shown through a centralized web dashboard.
Take Charge is a proof of concept for the idea that any USB charger could in fact be a disguised device that could install malware on an Android phone without any user intervention.
Implementation
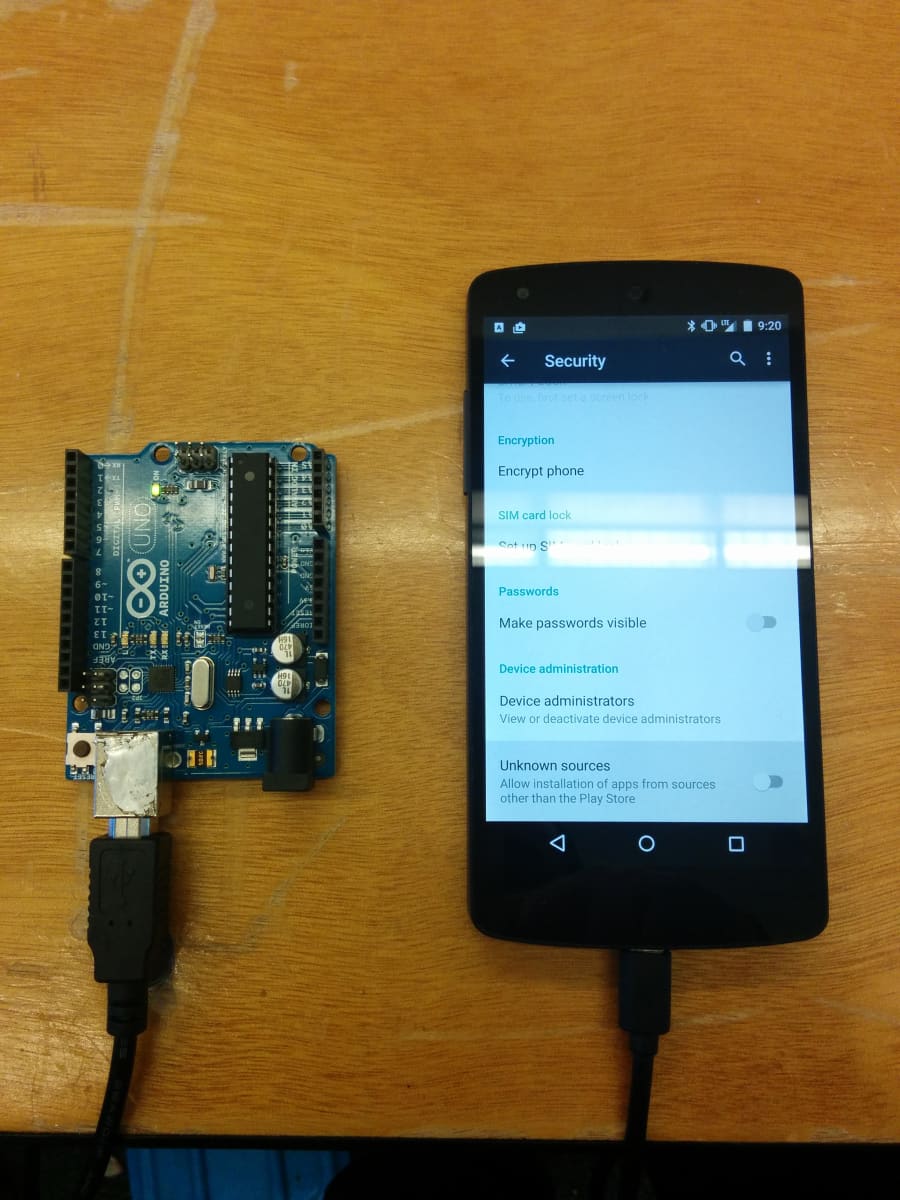
We used an Arduino connected to a USB OTG cable to emulate a USB keyboard. The Arduino sends keystrokes to enable Unknown Sources in Android Security settings, download and install the APK, and enable Notification Access for that APK.
As soon as the app is granted notification access, the service starts up in the background. It removes traces of itself from downloads and continues to run in the background, restarting on boot.
The service uploads all of the user's contacts, the list of apps installed on the phone, details about the Android device, and records all notifications and sends them to our web service in real time.
The app is undetectable to most users; there is no launcher icon, and no visual evidence that the app is running on the device
Dashboard
Our web dashboard offers an overview of all users with exploited devices, and offers a real-time view of data including notifications, contacts, and device stats. A real-time map shows the user's current location.




Log in or sign up for Devpost to join the conversation.